Find stealth daily.
#below command will show the files open by this user.
lsof -u username
# to check the activity of the connected ports via 80. Normally this port is used to attack other servers.
netstat -antp |grep :80
example
tcp6 0 0 2a01:4f9:2a:172d::47256 2800:6c0:2::23b:80 TIME_WAIT -
tcp6 0 1 2a01:4f9:2a:172d::38420 2a05:d014:9da:8c10:3:80 SYN_SENT 12000/[stealth]
tcp6 0 0 2a01:4f9:2a:172d::56094 2a02:4780:8:324:0:2a:80 TIME_WAIT -
tcp 0 1 95.216.22.210:56286 160.153.128.6:80 SYN_SENT 12000/[stealth]
tcp 0 0 95.216.22.210:35652 193.70.80.239:80 TIME_WAIT -
tcp 0 0 95.216.22.210:41460 108.178.48.234:80 TIME_WAIT -
tcp 0 0 95.216.22.210:43186 179.127.80.235:80 TIME_WAIT -
tcp 0 0 95.216.22.210:35592 188.164.195.229:80 TIME_WAIT -
tcp 0 0 95.216.22.210:80 40.77.167.76:27264 ESTABLISHED 4147/httpd
tcp 0 1 95.216.22.210:59738 91.215.216.29:80 SYN_SENT 12000/[stealth]
tcp 0 0 95.216.22.210:59248 91.146.103.138:80 TIME_WAIT -
tcp 0 0 95.216.22.210:59968 199.16.131.160:80 TIME_WAIT -
tcp 0 1 95.216.22.210:46400 198.54.112.252:80 SYN_SENT 12000/[stealth]
Now here the process 12000/stealth is attacking many ips on port 80.
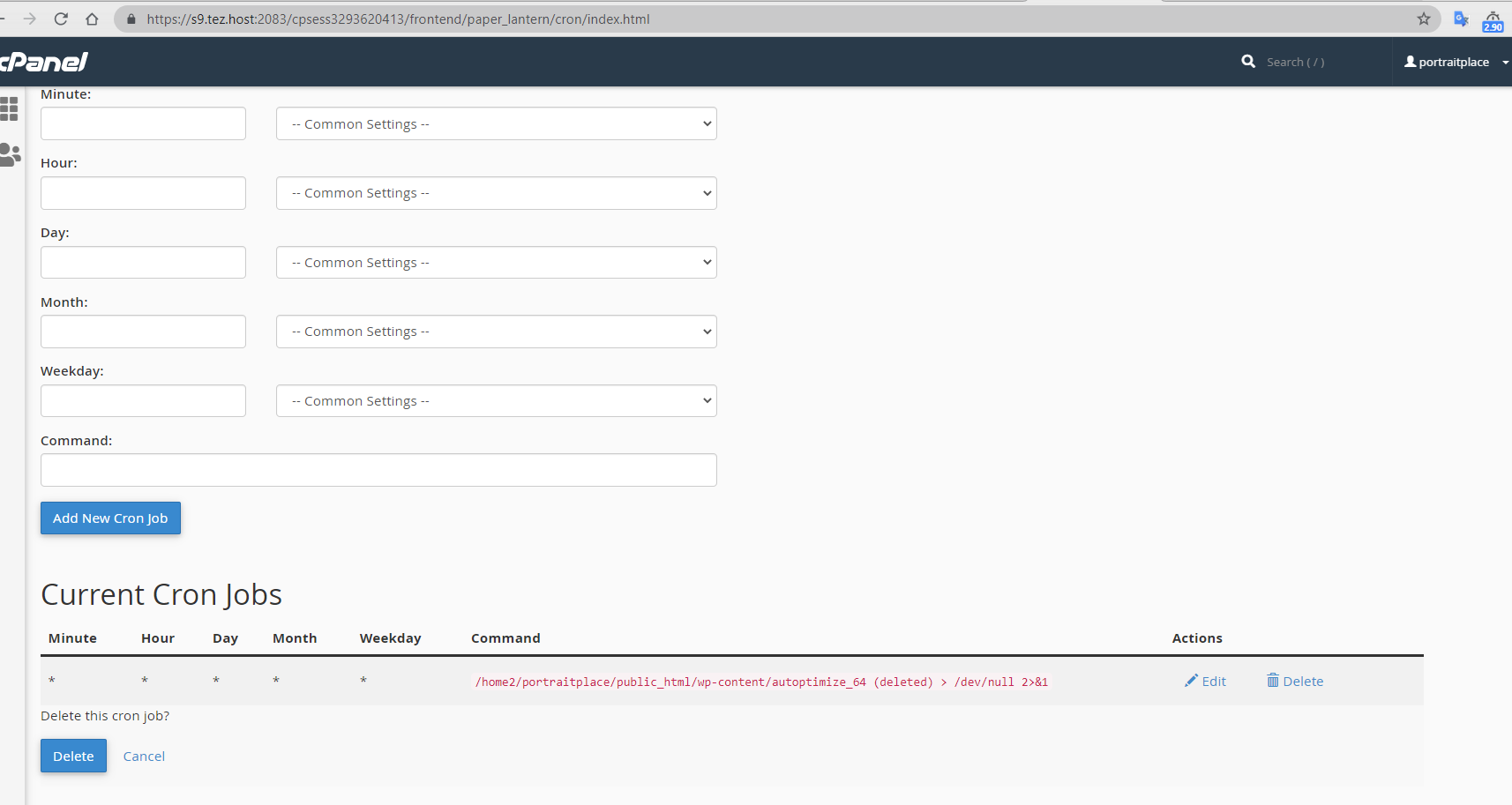
We identified that "portraitplace" user is the main culprit here. The process 12000 is of this user. Also the whm processes was showing the stealth process against user "portraitplace"
Suspend portraitplace user and create a ticket for it.
Also check the cron of this user, it will show you a process execution of every minute.